Introduction & Use Case:
You’re troubleshooting a mysterious bandwidth hog 🐖 in your network, only to discover that the culprit is the very same employee who asked you to look into it 😁❗ With March Madness just around the corner, that user is streaming the latest KY Wildcat basketball games on the ESPN app (Go Cats! 😺). You need to preserve bandwidth and maintain compliance… What do you do?
To make it more fun, this organization is operating on a shoestring budget and ad-hoc basis, so you cannot leverage Intune, SCCM, or GPO, but hey, users are Microsoft 365 A5 licensed.
In my experience, my favorite is the ‘scream test’ and it goes one of two ways if implemented correctly:
-
If they know they’re not supposed to have access, they’re not going to complain when it gets cut off 😉 .
-
You’ll see who screams and quickly learn how important the application you just disabled is to productivity 💲 💲 💲.
💡 Pro-Tip:Make sure to document that somewhere safe and accessible for the new kids on the block .
This blog post will guide you through deploying Defender for Cloud Apps from the ground up and integrating it seamlessly with Microsoft Defender for Endpoint to effectively block or unsanction unwanted applications that don’t meet your requirements (SOC2, GDPR, PIPEDA, CMMC, NIST, just to name a few). This ensures your cloud infrastructure remains secure, compliant, effective, and cost-efficient (even if you’re just trying to conserve bandwidth during the sweet 16 🏀).
Whether you’re an IT/SecOps professional or a Security & Compliance enthusiast, this comprehensive guide will provide you with the Defender for Cloud Apps knowledge and insights you need to identify and keep those bandwidth hogs at bay🐽, lock down your environment🔒, and knock those compliance scores out of the park ✅

In this Post We Will:
- ⚡ Deploy Defender for Cloud Apps.
- 🔧 Integrate with Defender for Endpoint.
- 🔌 Onboard a Device to Defender for Endpoint.
- ✔ Confirm our Defender for Endpoint AV Configuration pre-requisites without Intune, SCCM, or GPO (spoiler alert: it’s powershell).
- 🔍 Investigate Application Usage
- 🚫 Un-sanction an Unwanted Application.
- 🚧 Un-sanction an unwanted Application on your Firewall (for devices that don’t support the MDE agent).
- 💡 Ian’s Insights.
Deploy Defender for Cloud Apps
-
Ensure you have the necessary administrative permissions to configure and manage MDCA.
-
Access the unified security portal at www.security.microsoft.com.
-
Navigate to settings blade towards the bottom of the left menu and select Cloud Apps.
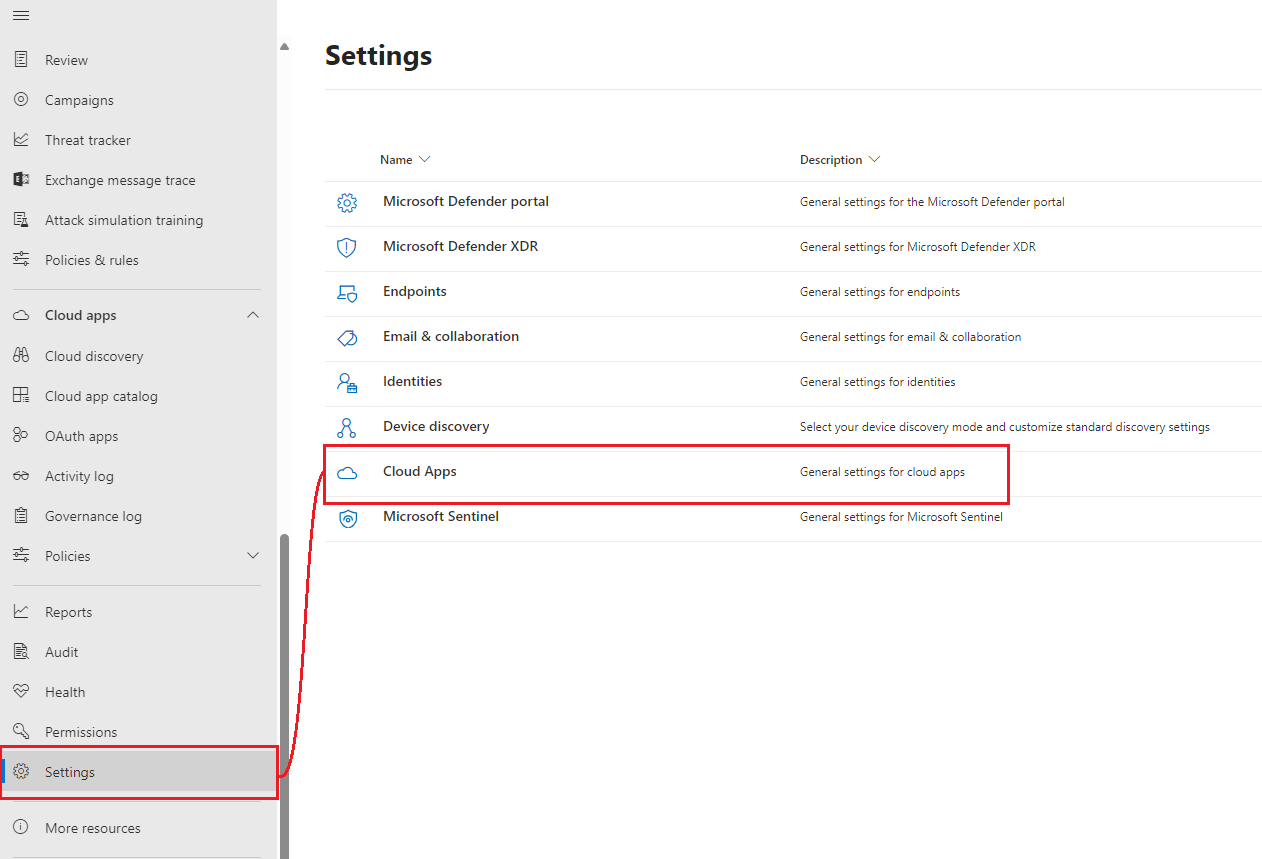
-
Scroll down to Microsoft Defender for Endpoint and check the Microsoft Defender for Endpoint Integration box.
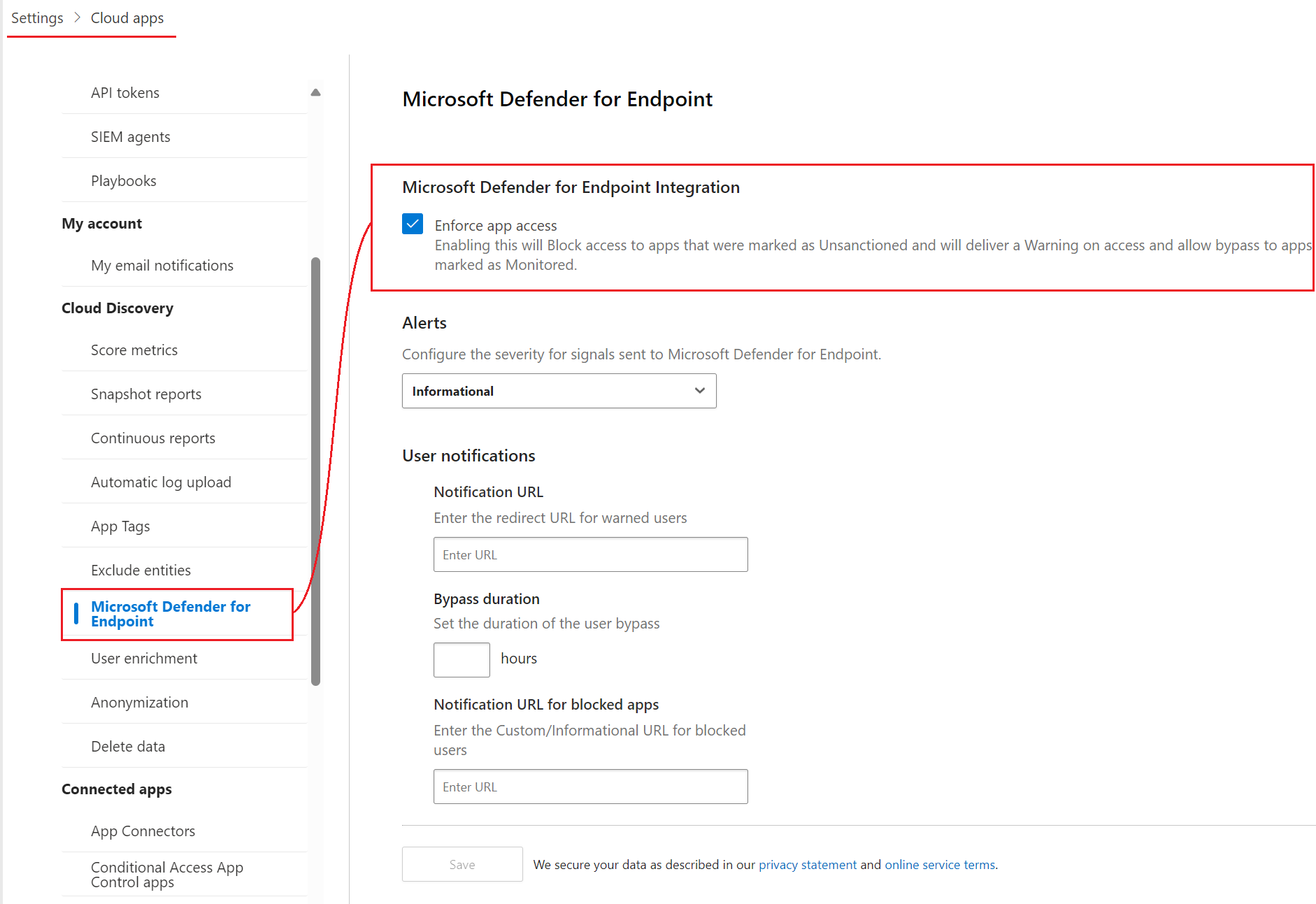
-
This integration allows for enhanced threat detection and response capabilities by correlating signals from endpoints and cloud apps.
-
If the Defender for Endpoint agent is deployed on devices within your organization, then MDCA can leverage the MDE agent to monitor network activities and traffic, including those related to cloud apps.
-
The Defender for Endpoint agent collects detailed information about cloud app usage directly from the endpoints. This includes data on which apps are being accessed, by whom, and from which devices and IP addresses etc.
Integrate with Defender for Endpoint
-
Access the unified security portal at www.security.microsoft.com.
-
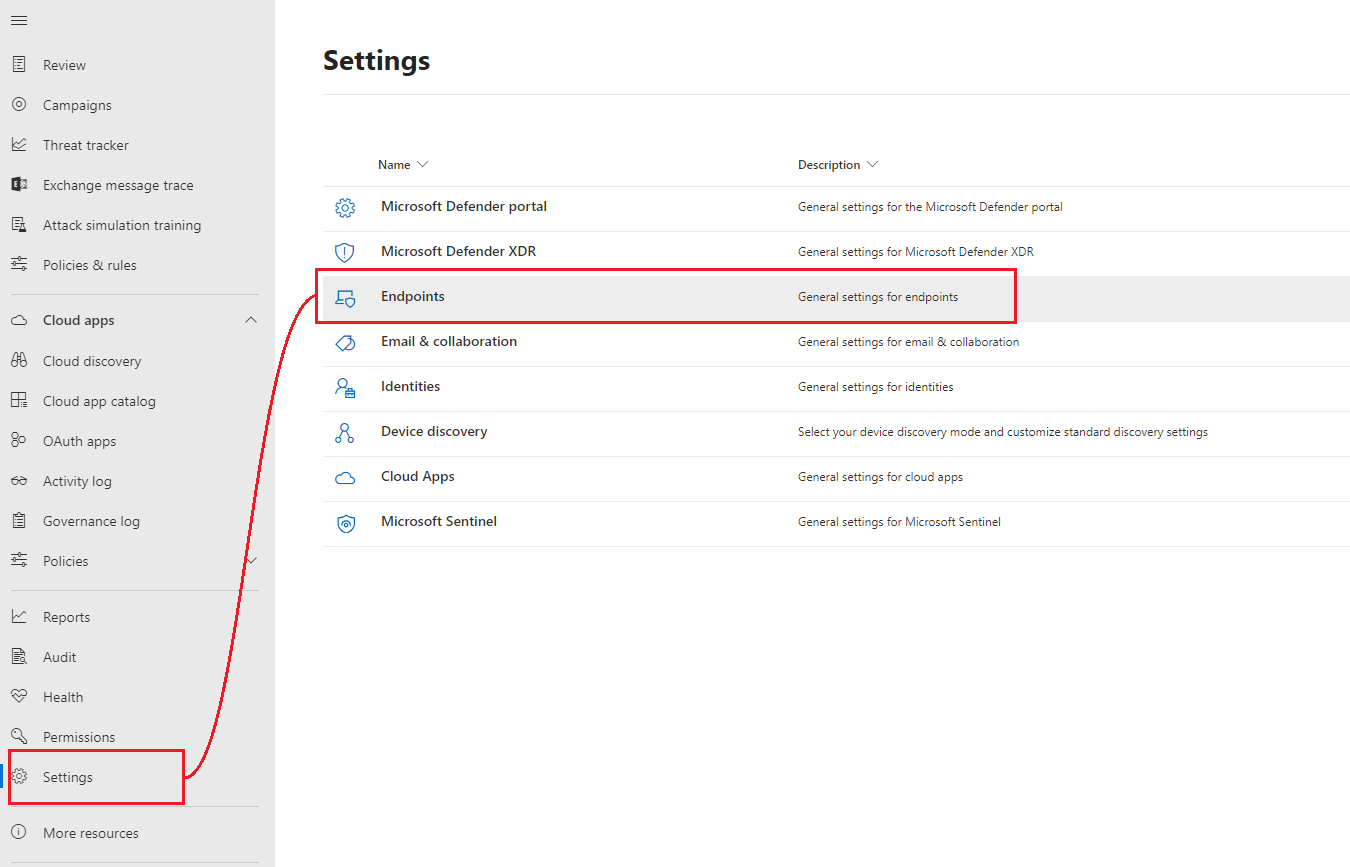
Navigate to settings blade towards the bottom of the left menu and select Endpoints.
Click on Advanced Features under General and toggle the Microsoft Defender for Cloud Apps Toggle switch to On as illustrated below:
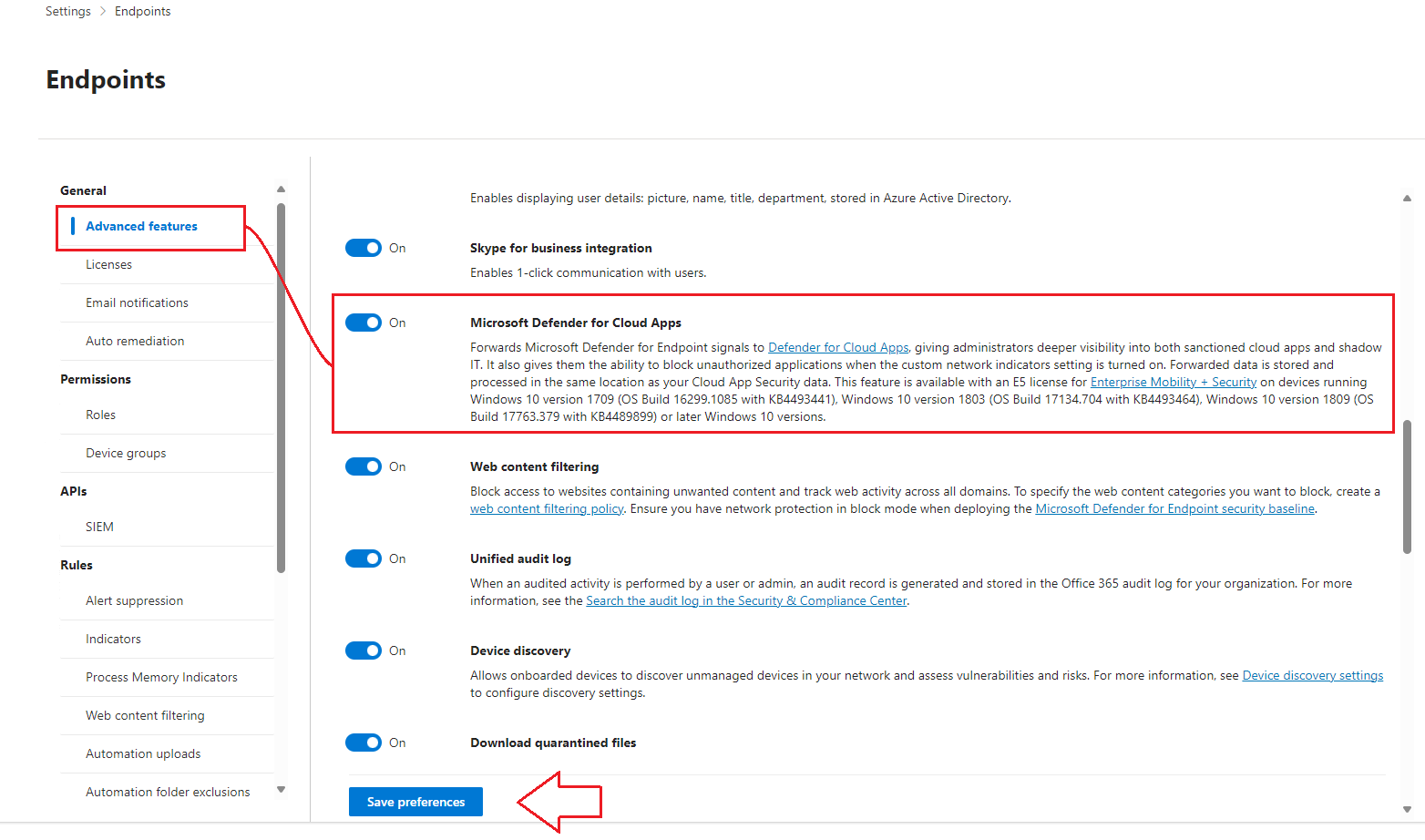
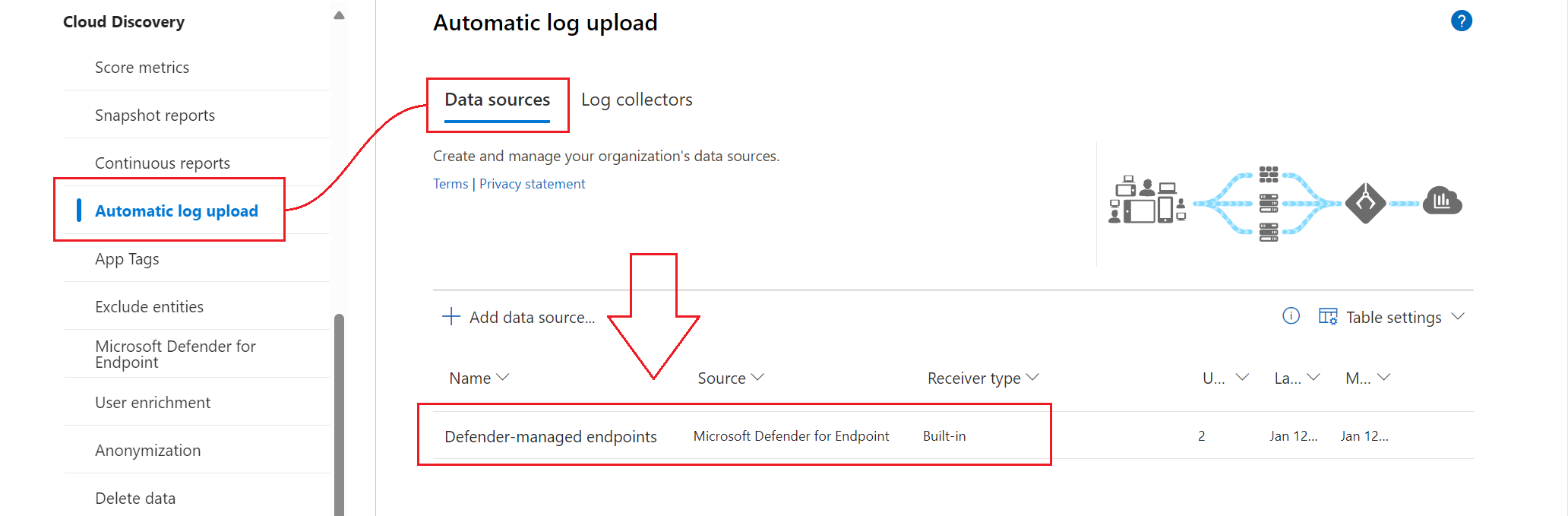
- Enabling this feature sends telemetry collected by Defender for Endpoint over to Defender for Cloud Apps. You can confirm by going back to the unified security portal » Settings » Cloud Apps » Automatic Log Upload and verifying the following entry populates (it can take a few hours for data to populate):
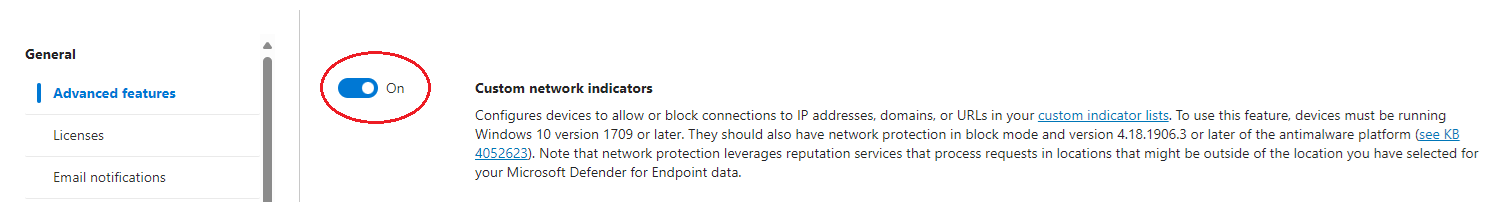
💡 While you’re in here, you’ll need to toggle Custom Network Indicators to the On position:
Onboard a Device to Defender for Endpoint
So perhaps you don’t have all of your devices onboarded to Defender for Endpoint, but you have a fair idea of who might be consuming all the bandwidth and want to start there. Follow the steps below to onboard their devices to Defender for Endpoint and get Cloud App Telemetry:
-
Logon to your device
-
Navigate to the unified security portal at www.security.microsoft.com from your device
-
Select the Settings blade from the left menu, then choose Endpoints

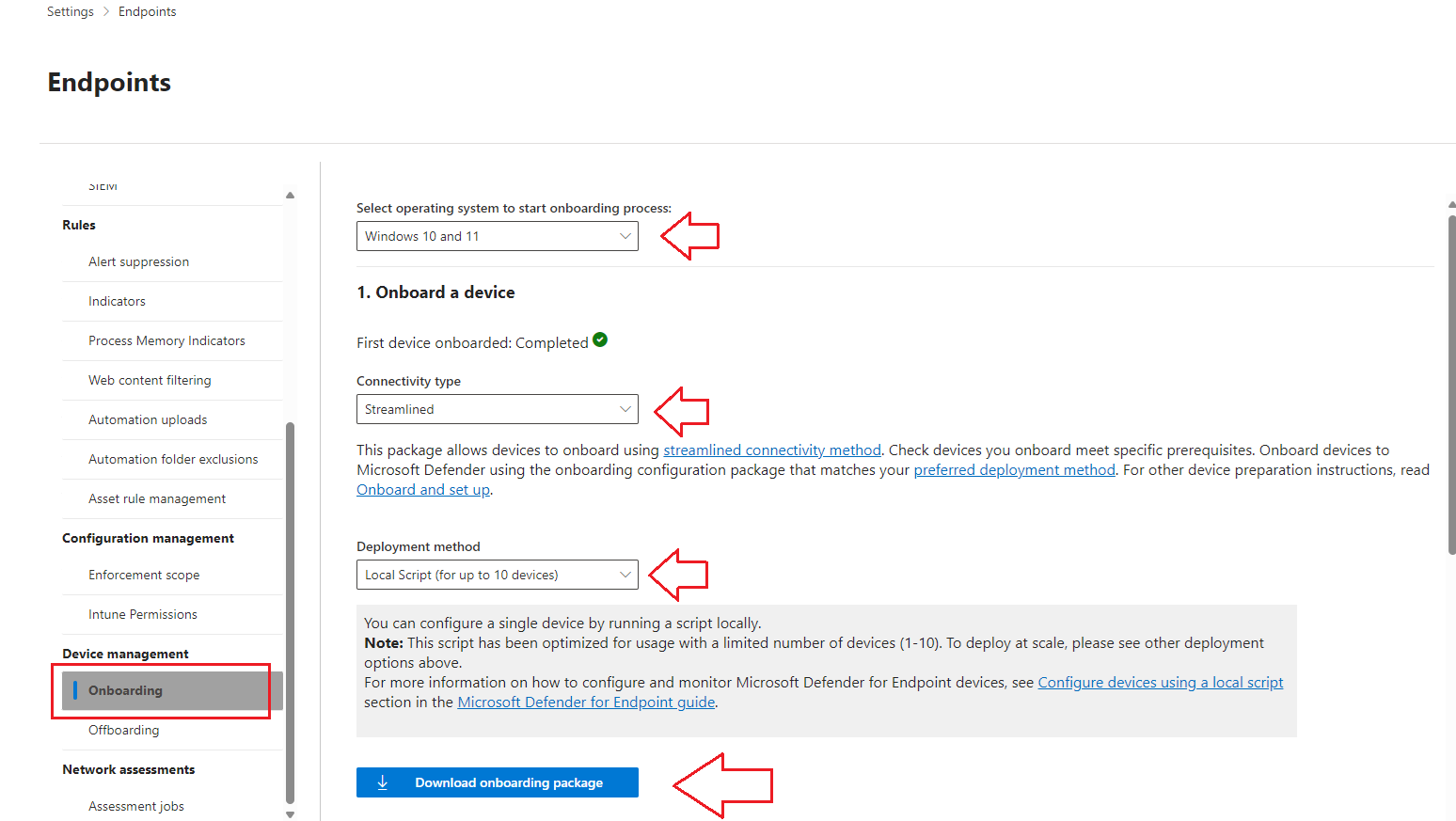
- Scroll down to Onboarding and fill out the appropriate settings, then download the onboarding package
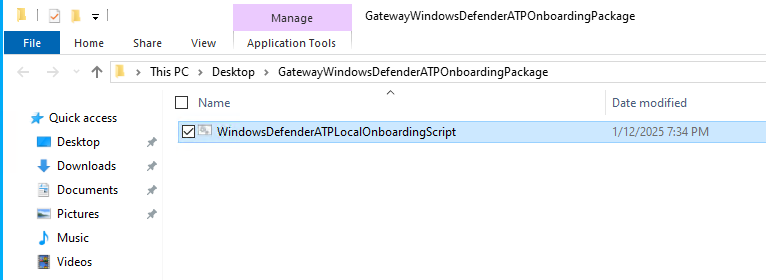
- Run it with administrative privilges on the device you wish to onboard.
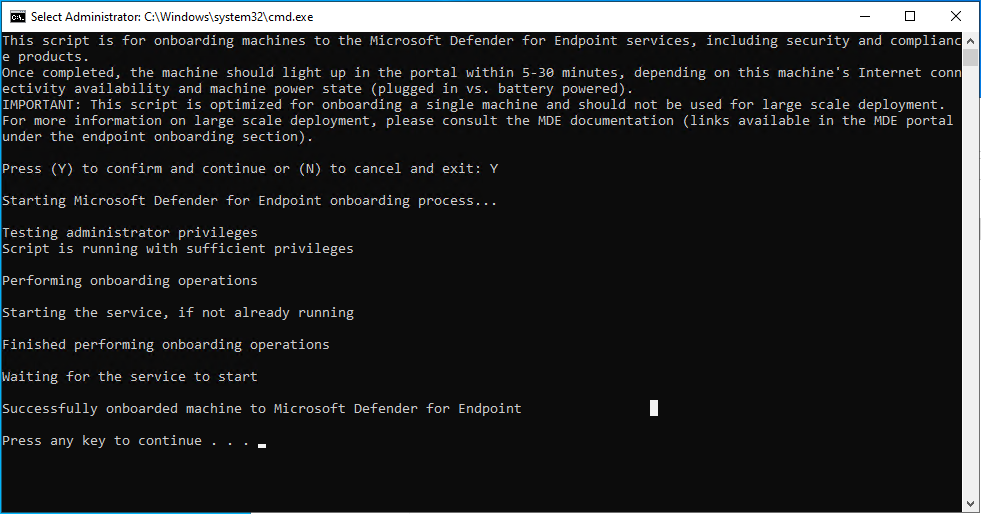
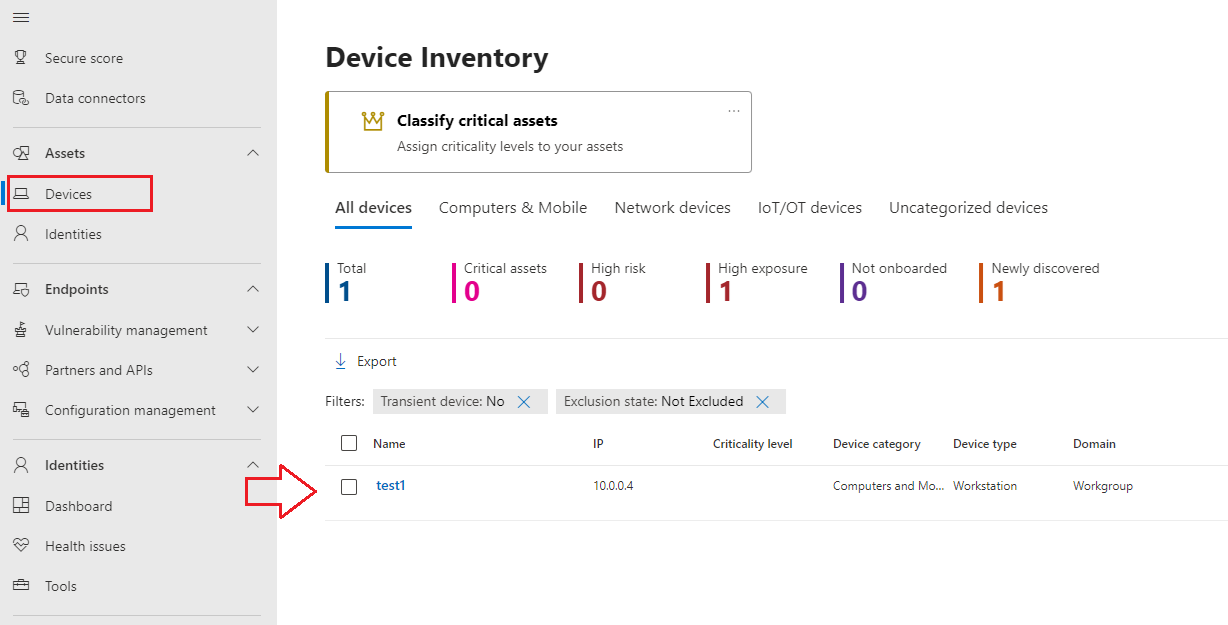
- Give it a few minutes and the device will show up in the unified security portal, illustrated below:
Confirm Defender for Endpoint AV Configuration Pre-Requisites via Powershell
-
Logon to your device
-
Launch Powershell as an administrator
-
Run the following command:
Get-MpComputerStatus
- Confirm the following pre-requisites are met:
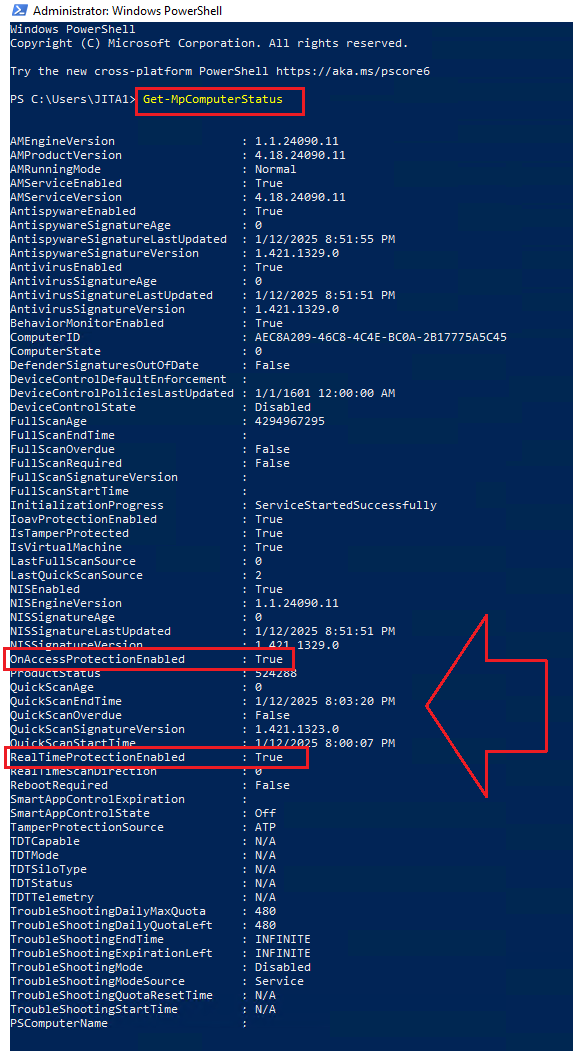
If either of these are False then use the following command to set them:
Set-MpComputerStatus
Here’s a list of available commands for reference
💡 Alternatively, you’d have to use Intune, Group Policy, SCCM, or a combination thereof to onboard and configure your fleet.
Investigate Application Usage
Let’s see who our heavy hitters are on the network.
Navigate to the Cloud Discovery blade, then go to the Discovered Apps tab to list applications found on your endpoints. You can sort these by traffic and uploaded data etc. to narrow down your hunt:
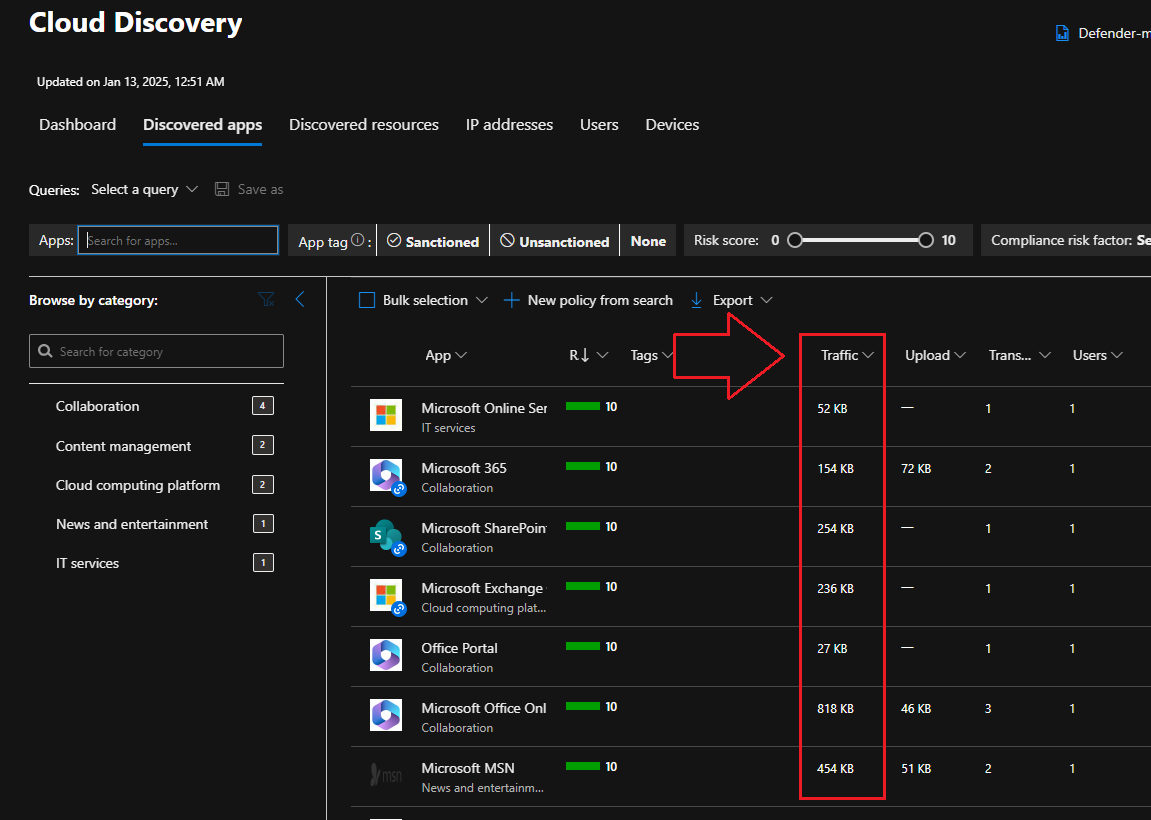
I spun up a vm for a couple hours just for this blog post so this traffic is not indicative of a typical production environment. For this example, lets open the Microsoft 365 app from the Discovered Apps tab to see it’s details, including it’s Cloud App score. This is great for compliance purposes. As illustrated, the Microsoft 365 app is compliant with GDPR, SOC, ISO 27001, ITAR, FINRA, to name a few:
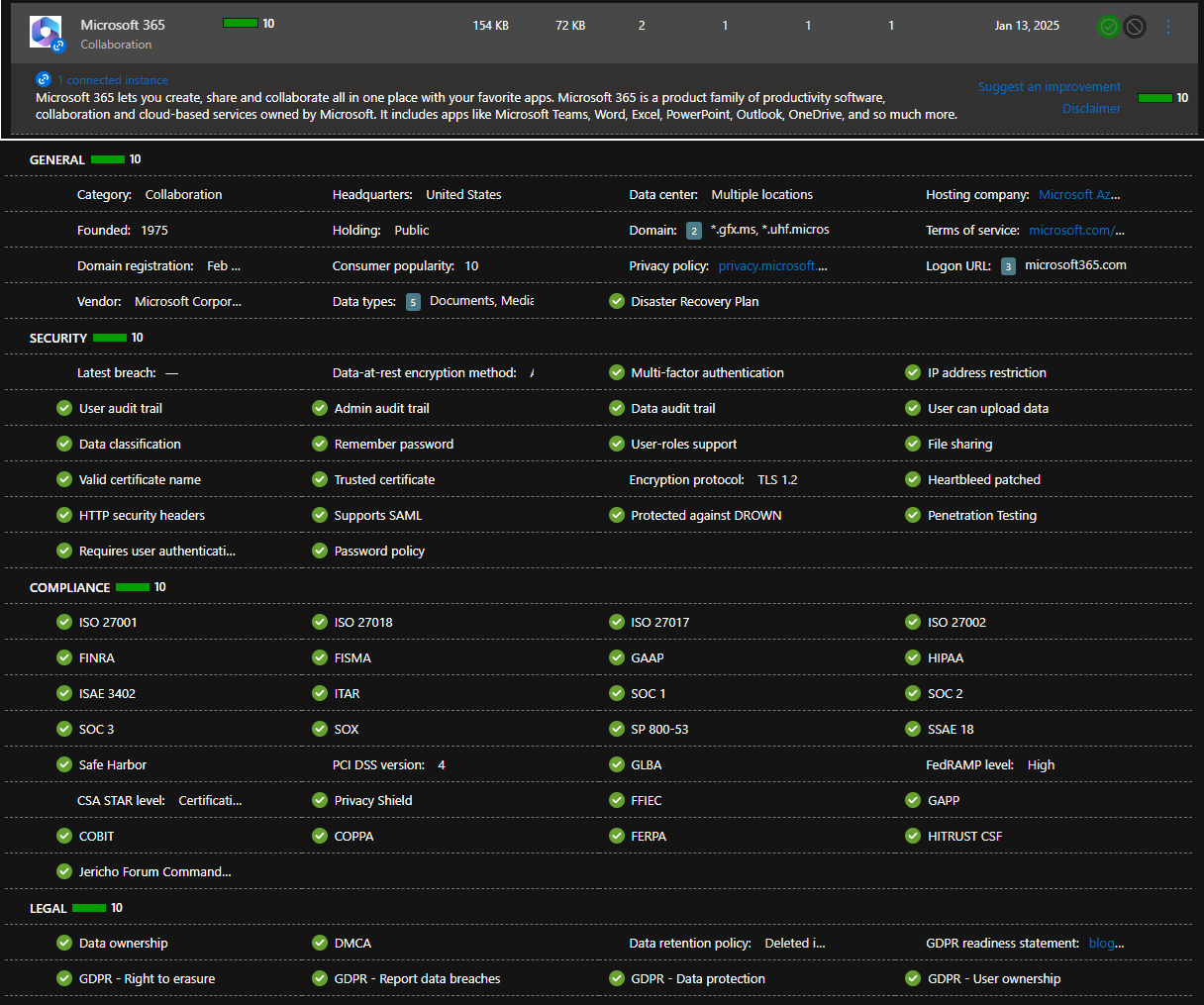
Click into the app from the list to bring up additional metrics:
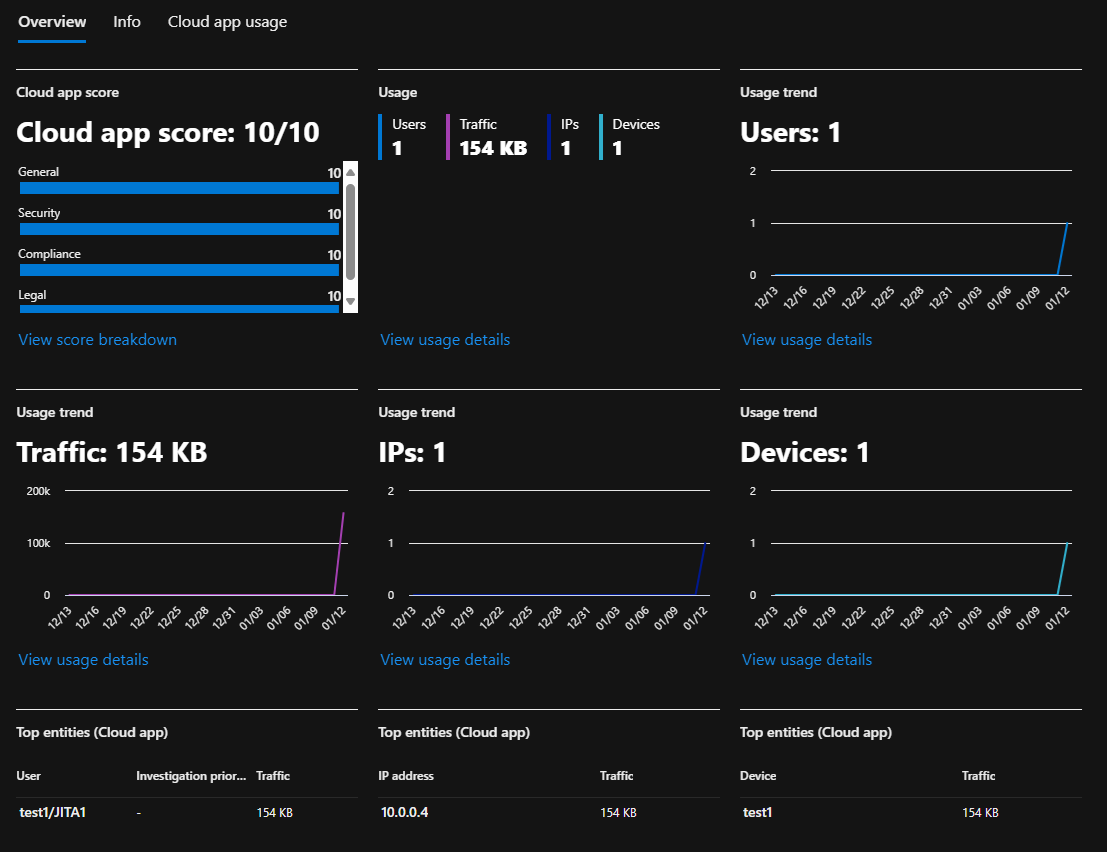
Lastly, slide over to the Cloud App Usage tab to identify usage by user:
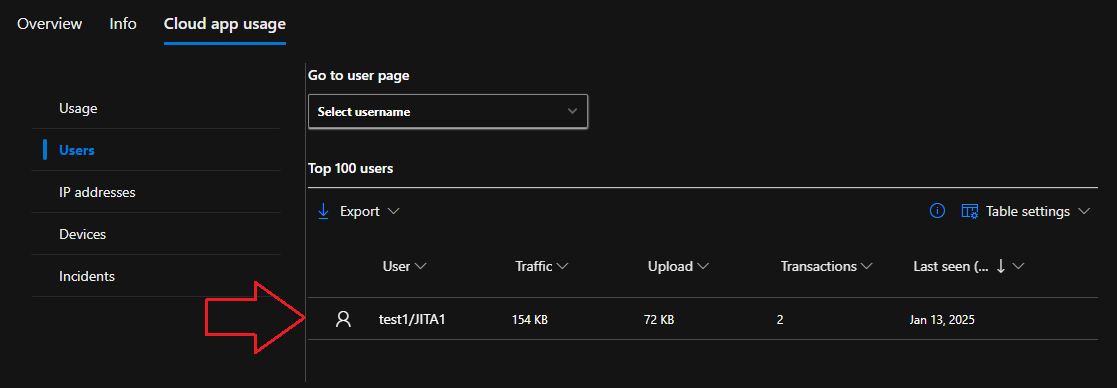
💡 This is helpful when deciding what applications to unsanction. If the entire corporation is heavily using an application then maybe investigate further before unsanctioning it and start with a small deployment group before unsanctioning it for everybody. There was one instance where unsanctioning the Steam Games platform locked a developer out of his Unreal Engine dev tools and was necessary for production. Always do your due diligence before initiating your own ‘scream’ test. On a side note, I’m a firm believer in Read-Only Fridays 😉.
Un-sanction an Unwanted Application
Now that we’ve got our devices onboarded and our MDE and MDCA platforms integrated, we can enforce MDCA polcies like blocking un-sanctioned applications using the MDE agent directly.
-
From the unified security portal, navigate to the Cloud Discovery Blade, located under Cloud Apps
-
Swing over from the Dashboard tab to the next one to the right, called Discovered Apps to list all of the applications reported from Defender for Endpoint that have run on that device since the Automatic Log upload has been deployed from MDE to MDCA earlier:

- You can Un-sanction any application found in your environment from here.
💡 Why wait until an application is already active in your environment to block it? The Cloud App Catalogue blade (directly underneath the Cloud Discovery blade) lists all of the applications that Microsoft has evaluated, and there’s thousands of them!
- In this example, we’ll block applications we know we don’t want to see in our network. From the Cloud App Catalogue search for your unwanted applications and select the Unsanction button to the right for each application you want to block:
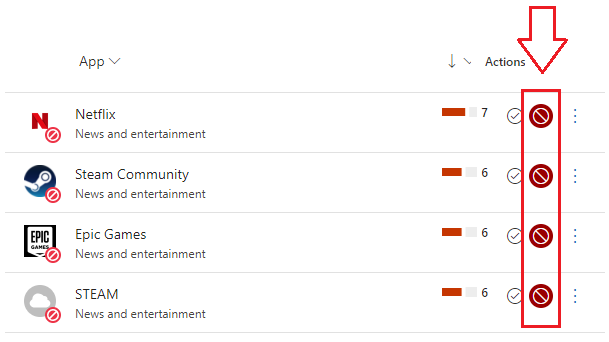
Give it a few minutes and try to navigate to one of those applications in a browser or through their designated local applications on a device that you’ve onboarded to MDE to see them fail (gloriously):
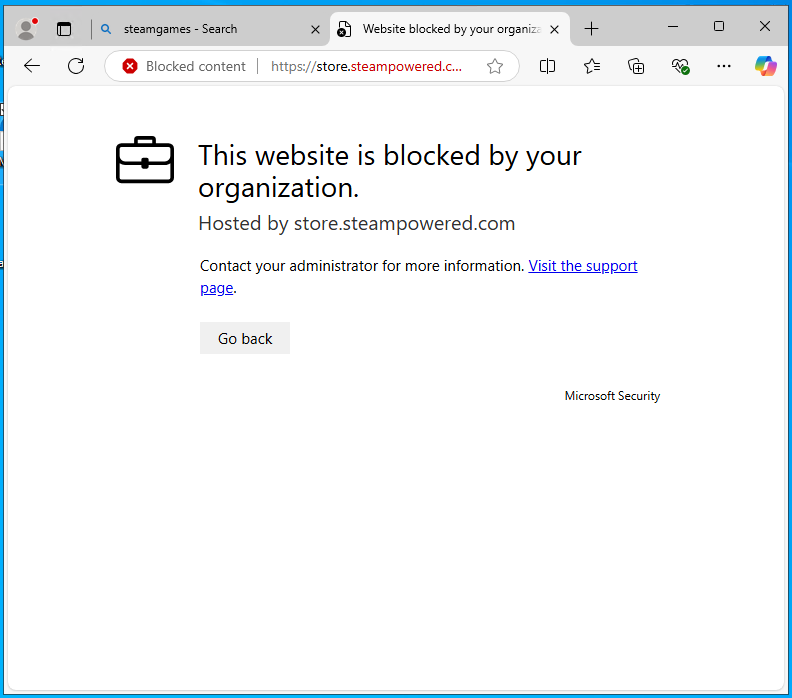
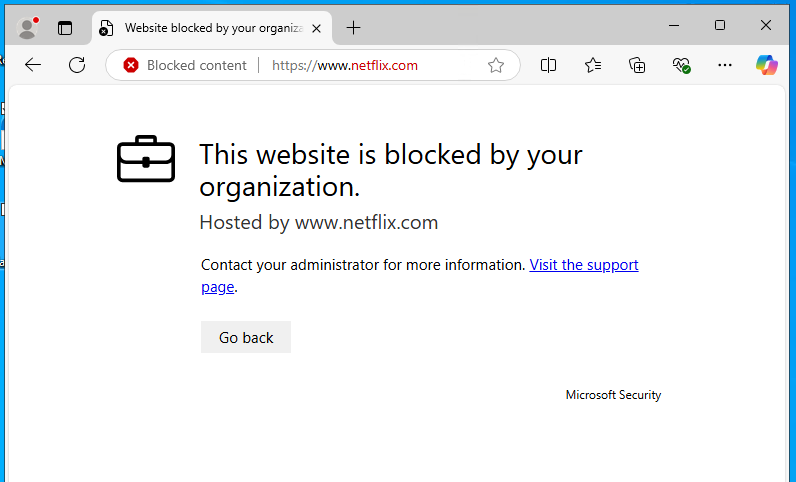
Un-sanction an unwanted Application on your Firewall (for devices that don’t support the MDE agent).
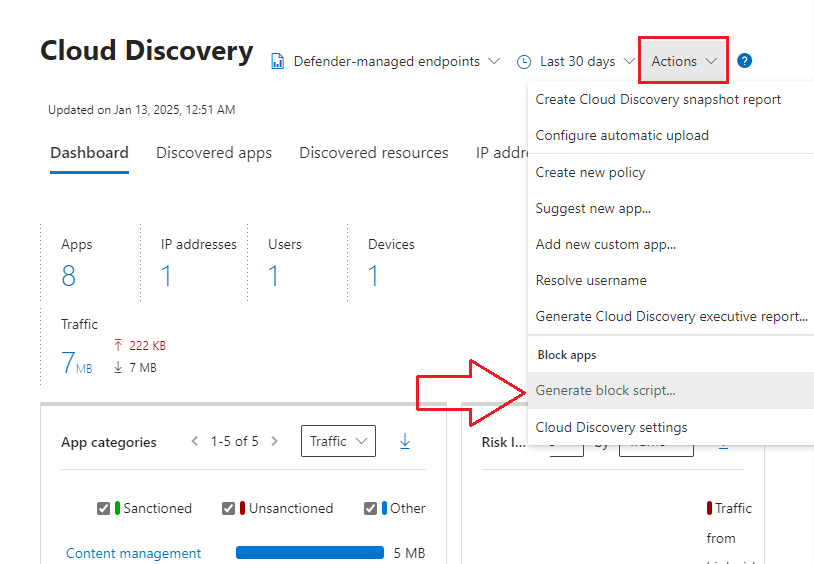
So what about those weird Linux distros that don’t support MDE (yet)… they need protection too right? If they’re behind a firewall appliance, check out this awesome MDCA feature that becomes available once you’ve un-sanctioned a few unwanted applications…
- From the Cloud Discovery Dashboard go to the Actions drop down, located in the top-right hand cornder of the screen, and click on Generate Block Script…:
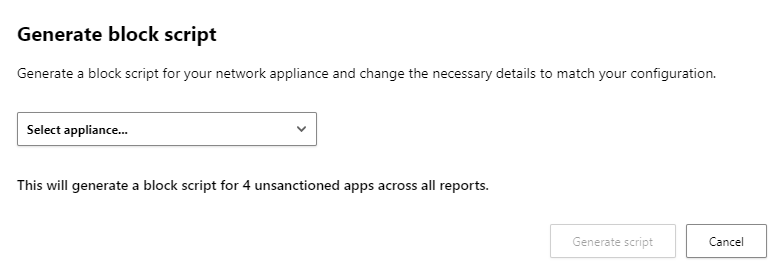
- Select your Firewall vendor:
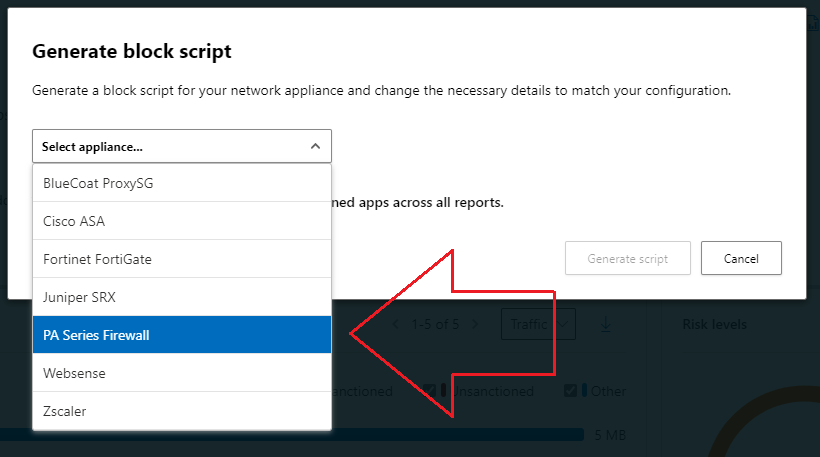
-
Copy and paste the output from a privileged exec state in your fireall to block the unwanted applications at the DNS level
-
Here’s an example output for a Palo Alto firewall that blocks Netflix, Steam Games, Epic Games, etc:
set application $serviceName1 category $pancategory subcategory $pansubcategory technology browser-based risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern epicgames.com
Set rulebase security rule rule$serviceName1 application $serviceName1 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern epicgames.com
Set rulebase security rule rule$serviceName1 application $serviceName1 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern api.epicgames.dev
Set rulebase security rule rule$serviceName1 application $serviceName1 from any to any action deny
set application $serviceName2 category $pancategory subcategory $pansubcategory technology browser-based risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern netflix.com
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern netflix.com
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern nflxvideo.net
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern nflxext.com
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern nflximg.com
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern netflixdnstest2.com
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern netflixdnstest3.com
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern netflixdnstest4.com
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern netflixdnstest5.com
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern netflixdnstest6.com
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern netflixdnstest7.com
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern netflixdnstest8.com
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern netflixdnstest9.com
Set rulebase security rule rule$serviceName1 application $serviceName2 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern netflixdnstest10.com
Set rulebase security rule rule$serviceName2 application $serviceName2 from any to any action deny
set application $serviceName3 category $pancategory subcategory $pansubcategory technology browser-based risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern store.steampowered.com
Set rulebase security rule rule$serviceName1 application $serviceName3 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern store.steampowered.com
Set rulebase security rule rule$serviceName1 application $serviceName3 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern api.steampowered.com
Set rulebase security rule rule$serviceName1 application $serviceName3 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern test.steampowered.com
Set rulebase security rule rule$serviceName1 application $serviceName3 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern crash.steampowered.com
Set rulebase security rule rule$serviceName3 application $serviceName3 from any to any action deny
set application $serviceName4 category $pancategory subcategory $pansubcategory technology browser-based risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern steamcommunity.com
Set rulebase security rule rule$serviceName1 application $serviceName4 from any to any action deny set application $serviceName category $pancategory subcategory $pansubcategory technology browser-baes risk $panrisk signature s1 and-condition a1 or-condition o1 operator pattern-match context http-req-host-header pattern steamcommunity.com
Set rulebase security rule rule$serviceName4 application $serviceName4 from any to any action deny
Ian’s Insights:
Ever use a DNS Sink Hole like a Pi-Hole (raspberry Pi powered)? This functioned pretty much the same way by refusing to resolve addresses known to host the application we are blocking. A Pi-Hole will actually resolve the addresses but send the results to an IP that doesn’t exist (hence “sinkhole”). Web pages load faster when they don’t have to resolve all the “junk” ads from IP’s known to host rubbish etc.
What happens if someone has already downloaded the Steam Games app and signed in before you’ve unsanctioned the application? Because they’ve signed in, the app has already ‘phoned home’ and retrieved a new token for authentication. The application will continue to work until the token expires and the app is forced to try and phone home for a new key and gets intercepted when it tries to resolve to the address block associated with Steam Games, at which point it will fail. This means that a user could potentially continue to use an un-sanctioned application temporarily until it’s token expires.
Lastly, consider going to the unified security portal » settings » cloud apps » Exclude Entities and adding an exclusion so you can watch the finals 😜
In this Post We:
- ⚡ Deployed Defender for Cloud Apps.
- 🔧 Integrated with Defender for Endpoint.
- 🔌 Onboarded a Device to Defender for Endpoint.
- ✔ Confirmed our Defender for Endpoint AV Configuration.pre-requisites without Intune, SCCM, or GPO (spoiler alert: it was powershell).
- 🔍 Investigated Application Usage
- 🚫 Un-sanctioned an Unwanted Application.
- 🚧 Un-sanctioned an unwanted Application on your Firewall (for devices that don’t support the MDE agent).
Thanks for Reading!
I hope this was a much fun reading as it was writing. What will you block from your environment first?

Helpful Links & Resources:
-
https://learn.microsoft.com/en-us/powershell/module/defender/?view=windowsserver2025-ps#defender
-
https://learn.adafruit.com/pi-hole-ad-blocker-with-pi-zero-w/install-pi-hole
-
https://learn.microsoft.com/en-us/defender-endpoint/configure-endpoints-script

